Your browser doesn't support the features required by impress.js, so you are presented with a simplified version of this presentation.
For the best experience please use the latest Chrome, Safari or Firefox browser.
Please give a careful analysis of the sparse vector technique, comparing your formalization with the differential privacy book and the previous formalizations in [A1,A2].
Overview
Background
Preliminaries
Above Threshold (Dwork and Roth)
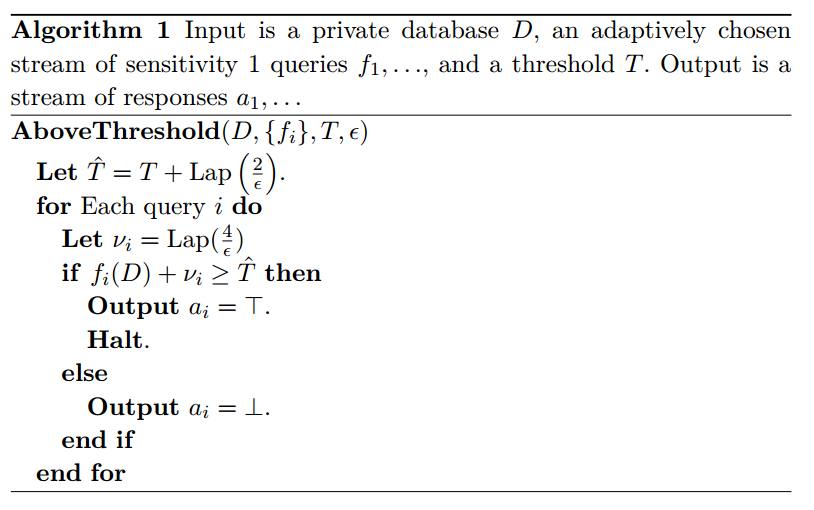
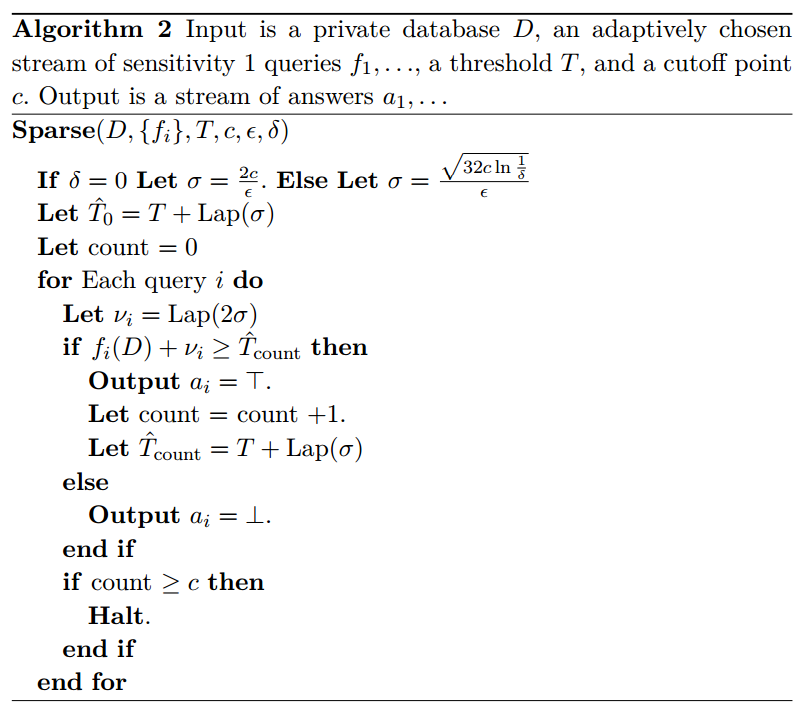
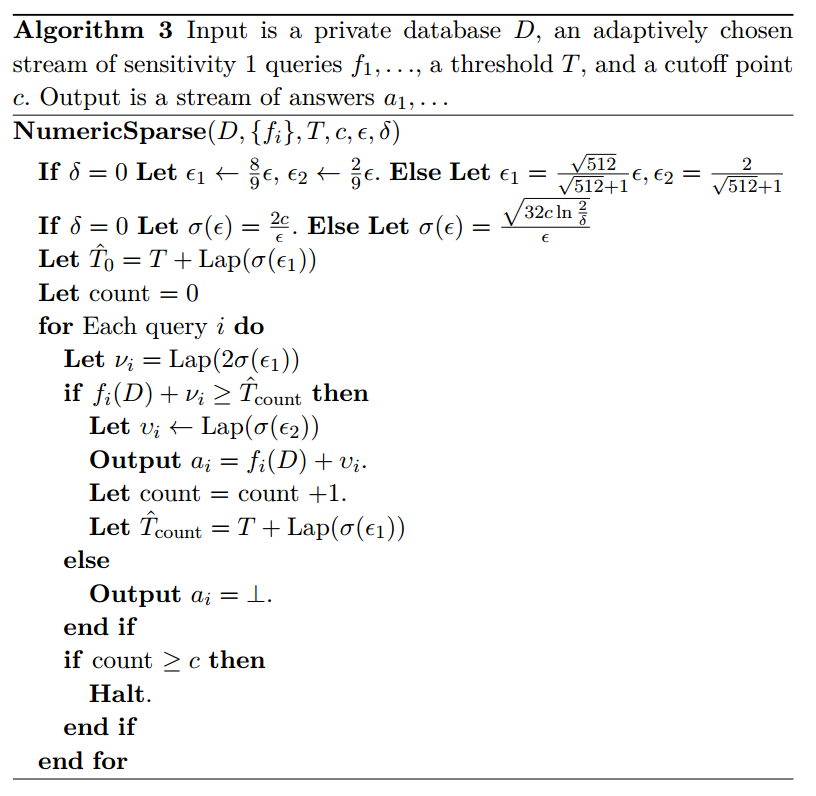
Above Threshold (Barthe et al.)

Between Thresholds (Barthe et al.)
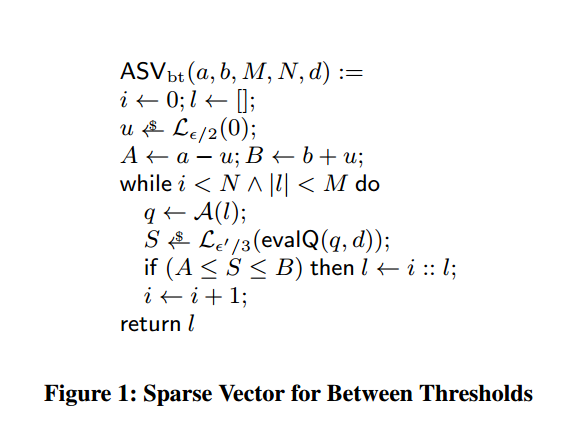
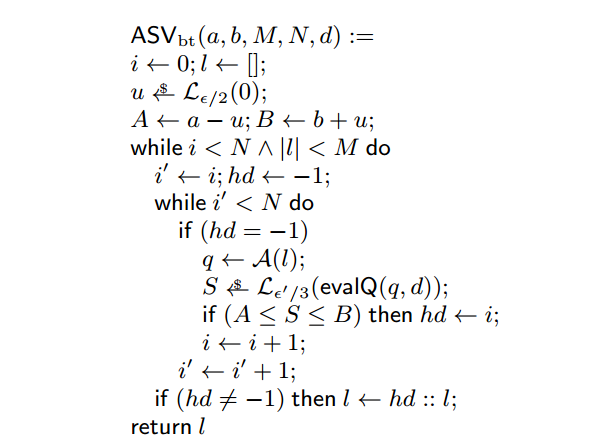
From monolith to composition
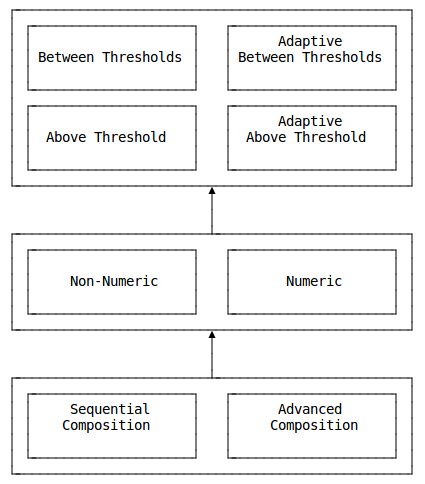
Logical Proofs
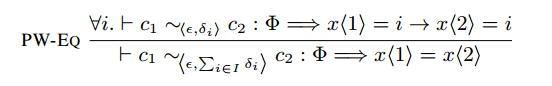
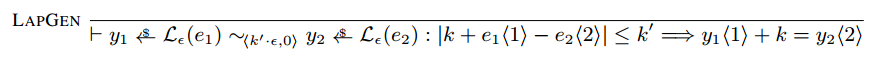
EasyCrypt Implementation
Use a spacebar or arrow keys to navigate